COmanage Registry can be used to enable users to upload and manage their public SSH keys. Registry can be configured to provision these keys to LDAP so that they may be used by other systems. This recipe describes how COmanage Registry might be configured to accomplish this goal.
Recipe Ingredients
- This recipe requires COmanage Registry version 3.3.0 or later.
- Assumes the presence and use of an LDAP server.
- Install Plugins
Install the Authenticator Plugin - Configure Authenticator
Configure an Authenticator for SSH - Enable user feature
Enable users to add/manage their SSH Key(s)- Via their profile
- Via an enrollment flow
- Configure Provisioner
Provision SSH keys to LDAP - REF: Configure your system to use stored keys
Like what you see? See our other recipes!
Recipe Steps
1. Install Plugins
COmanage Registry supports several types of plugins in order to easily customize and extend Registry functionality. Each plugins may be one of three types, each of which has a different process for being installed and enabled: Supported Core Plugins, Supported Non-core Plugins, and External Plugins.
2. Configure Authenticator
All plugins have basic settings that are are related to the plugin’s Class. In addition, some plugins have plugin-specific settings to configure the specifics related to the plugin.
3. Enable Registry to collect SSH Keys
By adding an authenticator via the plugin, you have enabled the collection of public SSH keys on any CO Person record. You may enable users to add their SSH keys to their CO Person record in Registry 1) Via their profile, or 2) Via an enrollment flow
You may also use the Registry API to add SSH keys. Resources for the SshKey API can be found in the [ Recipe Variations and Complements ] section of this document.
3.1 Collect SSH Keys via the user's profile
- Sign into Registry and navigate to the CO (if necessary)
- Open one's profile for the CO
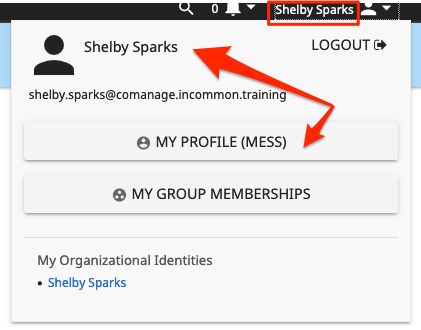
The user clicks their name in the upper right corner of the screen to display their user options, The user clicks the "My Profile" button to display their profile - Manage the user's the list of Authenticators
Click the [ Authenticators ] link located in the box on the right side of the window to display a list of authenticator types that the user may add
Click the [ Manage ] button next to the authenticator that you have configured to display the group of authenticators that are associated with this authenticator configuration. From this list, you may add new keys and [ View ] or[ Delete ] existing ones. - Add a Public SSH Key
Click the[ Add SSH Key ] link above the table on the right to display a form to add a new authenticator.
On the form that opens, click the [ Choose File ] button to locate your public SSH key on your computer, and the btn:[UPLOAD] button to add the key to the CO Person profile. This action will check if the uploaded file appears to be a public SHH key before adding it.
3.2 Collect SSH Keys via an enrollment flow
As of Registry v3.3.0, Authenticators may be collected as part of an Enrollment Flow.
To add SSH key collection to an enrollment flow:
- Navigate to the enrollment flow that should manage SSH Key collection
Click the [ Edit ] button for the enrollment flow to which you would like to add the SSH collection step. Configure the flow to include SSH Key collectrion
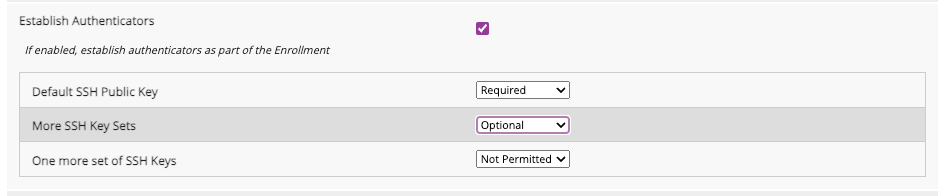
Near the bottom of the enrollment flow configuration form, check the [ Establish Authenticators ] checkbox to display the list of active, configured Authenticators. For each Authenticator, select [ Required ], [ Optional ], or [ Not Permitted ] to affect your needs for SSH key upload.Although the image above displays three different SSH Key configurations, most implementations will only use one. SSH Authenticators are multi-valued, so multiple keys may be associated with each configuration.Save your enrollment flow
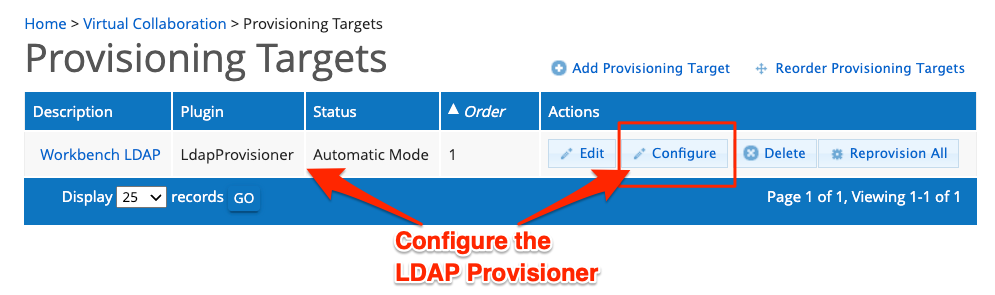
4. Configure Provisioner
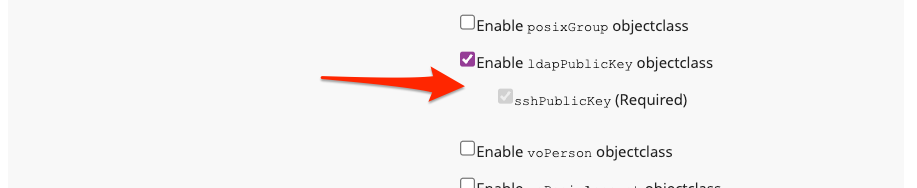
Once Public SSH Keys are stored within Registry, they may be provisioned via any provisioner plugin that supports they keys. The LDAP Provisioner is one of these plugins.
5. Configure your systems to use the stored keys (REFERENCE ONLY)
FOR REFERENCE ONLY
These instructions in this section are NOT intended to provide instruction or guidance on system, security, or LDAP configurations.
At all times, you should consult to your security guidelines and seek the advice of experts to implement a solution that achieves your security and access goals. The resources in this section are designed ONLY to provide links to what might be helpful references.
Recipe Variations and Complements
SSH Key API
You may explore the _experimental_ SshKey API for managing SSH keys. For additional information, see the following resources:
- SshKey API (Reference Page)
- SshKey Schema (Reference Page)
Managing UNIX Clusters
A common use case for collecting and provisioning SSH Keys is for their use in UNIX clusters by the end user. The following resources provide additional information:
- LDAP Provisioning Plugin for information on configuring LDAP Provisioning to support UNIX Clusters.
- Unix Cluster Plugin (Experimental)
- About the voPerson Object Class