SAML Assertion Tools
The GridShib Authentication Assertion Client binds a SAML authentication assertion to a proxy certificate. This tool has two basic functions:
- issue an authentication assertion
- bind an assertion to a proxy certificate
These two functions need to be separated into two separate tools:
By separating out the binding capability of the current tool, we can reuse the SAML X.509 Binding Tool to implement a more powerful set of tools that leverage a Shibboleth !IdP configuration:
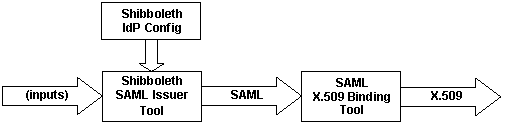
The Shibboleth SAML Issuer Tool issues a SAML attribute assertion and (optionally) a SAML authentication assertion based on the underlying !IdP configuration.
Finally, if we refactor the Shibboleth !IdP Tester so that it outputs a <saml:Assertion> element (instead of <saml:Attribute> elements), we obtain another tool (called the SAML Attribute Query Client) that can be used as yet another source of SAML assertions:
Thus our toolbox consists of four SAML Assertion Tools:
- Globus Toolkit SAML Issuer Tool
- Shibboleth SAML Issuer Tool
- SAML Attribute Query Client
- SAML X.509 Binding Tool
Being a command-line tool, the GT SAML Issuer Tool requires only Java and Ant. The Shibboleth SAML Issuer Tool requires Java, Ant, and a Shibboleth !IdP (but Apache and Tomcat are not required). The SAML Attribute Query Client implements the SAML Attribute Query Profile for X.509 Subjects, that is, it functions as a standalone attribute requester. The SAML X.509 Binding Tool takes any number of SAML assertions as input, and binds these assertions to an X.509 proxy certificate.
Globus Toolkit SAML Issuer Tool
The Globus Toolkit SAML Issuer Tool (Bug 4756) returns a <saml:Assertion> element containing a <saml:AuthenticationStatement> element.
Inputs:
$ --user=Name (required): Local principal name (username)
$ --relyingParty=URI (optional): Unique identifier of relying party (SP); if omitted, an unauthenticated SP is assumed
$ --config=URL (optional): Java properties config file (as file: URL)
$ --authn (optional): Indicates a <saml:AuthenticationStatement> element is required (default)
$ --authnMethod {{URI (optional): =AuthenticationMethod}} URI (requires =--authn=)
$ --authnInstant {{Date (optional): =AuthenticationInstant}} (requires =--authn=)
$ --ssoResponse {{URL (optional): File containing a =<samlp:Response>}} element (as file: URL)
$ --lifetime=Secs (optional): Lifetime (in seconds) of the SAML assertion
$ --x509 (optional): Indicates <saml:Assertion> element is to be bound to an X.509 proxy certificate
$ --x509lifetime (optional): Lifetime (in seconds) of proxy certificate (requires =--x509=)
$ --outfile=File (optional): File to output the SAML assertion (or proxy certificate)
$ --debug (optional): Indicates debugging mode
$ --quiet (optional): Indicates quiet mode
Output: <saml:Assertion> element (or X.509 proxy if --x509 set)
Features:
- Java application with CLI and shell script wrapper
- Java properties file specified with
--configinput option - Produces one SAML
<saml:Assertion>element, optionally bound to X.509 proxy certificate - Uses Globus SAML library to produce assertions
- Leverages SAML X.509 Binding Tool
- Ships with GridShib SAML Tools
Shibboleth SAML Issuer Tool
The Shibboleth Attribute Authority Tool (Bug 4752) is an extension of the Shibboleth resolvertest tool. The latter returns a sequence of <saml:Attribute> elements based on the configuration in resolver.xml or idp.xml . The Shibboleth SAML Issuer Tool extends resolvertest so that it returns a <saml:Assertion> element containing a <saml:AttributeStatement> element and (optionally) a <saml:AuthenticationStatement> element.
Inputs:
$ --user=Name (required): Local principal name (username)
$ --relyingParty=URI (optional): Unique identifier of relying party (SP); if omitted, an unauthenticated SP is assumed
$ --config=URL (optional): Java properties config file (as file: URL)
$ --authn (optional): Indicates a <saml:AuthenticationStatement> element is required (default)
$ --authnMethod {{URI (optional): =AuthenticationMethod}} URI (requires =--authn=)
$ --authnInstant {{Date (optional): =AuthenticationInstant}} (requires =--authn=)
$ --ssoResponse {{URL (optional): File containing a =<samlp:Response>}} element (as file: URL)
$ --lifetime=Secs (optional): Lifetime (in seconds) of the SAML assertion
$ --x509 (optional): Indicates <saml:Assertion> element is to be bound to an X.509 proxy certificate
$ --x509lifetime (optional): Lifetime (in seconds) of proxy certificate (requires =--x509=)
$ --outfile=File (optional): File to output the SAML assertion (or proxy certificate)
$ --debug (optional): Indicates debugging mode
$ --quiet (optional): Indicates quiet mode
Output: <saml:Assertion> element (or X.509 proxy if --x509 set)
Features:
- Java application with CLI and shell script wrapper
- !IdP home directory specified with
--configinput option - Produces one or two SAML
<saml:Assertion>elements, optionally bound to X.509 proxy certificate - Uses !OpenSAML V1.1 (bundled with the Shib !IdP) to produce assertions
- Leverages SAML X.509 Binding Tool
- Packaged as a Shib !IdP extension
SAML Attribute Query Client
The SAML Attribute Query Client (Bug 4754) is a refactoring of the Shib !IdP Tester that outputs a SAML attribute assertion.
Inputs: (see User Guide for Shib !IdP Tester)
Output: <saml:Assertion> element
Features:
- Java application with CLI and shell script wrapper
- Consumes whatever SAML
<saml:Assertion>elements are returned by the AA - Uses Globus SAML libary to produce queries and consume assertions
- Leverages SAML X.509 Binding Tool
- Ships with GT SAML Tools
SAML X.509 Binding Tool
The SAML X.509 Binding Tool (Bug 4755) binds one or more SAML assertions to a proxy certificate.
Inputs: one or more <saml:Assertion> elements
Output: X.509 proxy certificate
Features:
- Java API (no CLI)
- Produces an X.509 proxy certificate with bound SAML assertion(s)
- Packaged as one or more JAR files
- Ships with GT SAML Tools and Shib SAML Tools