This page has been deprecated and active content has been moved to this page.
| Info |
|---|
The three-year TIER program reached a successful conclusion at the end of 2018. The program, funded by 49 investor schools, involved containerizing and connecting the Internet2 Community’s key open-source Identity and Access Management software components, significantly reducing the time and effort needed for installation, configuration, and upgrades. The result is the new InCommon Trusted Access Platform, an IAM suite meeting the specific needs of research and education. Please visit the InCommon Trusted Access Platform wiki for more information, including links to software downloads. |
TIER: Production Releases
The TIER team is grateful for everyone who evaluates and uses these releases.
Docker Containers
| Info | ||
|---|---|---|
| ||
Shibboleth SP Linux httpd Container (3.0.3)
Shibboleth SP Windows IIS Container (3.0.3)
Grouper Linux Container (2.4.0)
Grouper Linux Container (2.3.0)
COmanage Linux Container (3.2.0)
midPoint Linux Container (3.9 Preview)
|
Virtual Machine Images
The links below are to virtual machine images, which are designed to be Docker build/run machines and are preloaded with the appropriate set of Docker containers. The VMs are intended primarily for campuses that do not currently operate container-based applications or are new to container-based applications. AMIs, for running in AWS, are also available here.
| Info | ||
|---|---|---|
| ||
COmanage Registry (3.1.1) Grouper (2.3.0) Shibboleth IdP VM (3.3.1) |
Amazon Machine Images (AMIs)
| Info | ||
|---|---|---|
| ||
If you will be using the released VMs, below are a few suggestions:
The VMs are designed to be run in VirtualBox. If you are not familiar with VirtualBox, you can read the documentation and download the software from the Oracle's web site.
AMIs, for running in AWS, are also available here.
Once VirtualBox is installed and running, you import the .ova distribution using the File / Import Appliance function.
The default network connection for some of the Virtual Machines is NAT. This works well if you want to log into and examine the VM and containers. But to connect to services hosted by the VM, you'll likely want to switch the network to bridged mode. This will give the VM an IP address from your network's DHCP server and provide you with the ability to access services from a browser.
Please review the Release Notes for installation instructions and additional information on VirtualBox setup.
Remember to change the login password(s) before you place the VMs on a public network.
TIER - Current State of Components
This document, TIER Accomplishments by Thematic Groups, provides the current state of the component portions of the TIER program and planned future activities. It draws from initial documentation of TIER program requirements and subsequent working group accomplishments. It also includes items flagged “[Must2018]” which have been identified by the component architects as being required to be completed before the end of 2018.
Need Basic Information?
Visit the TIER 101 page.
TIER Release Reports
Campus Practices Included in the TIER Program
NOTE:
Starting with the 17040 release, the TIER components contains functionality from phase 1 of the TIER Instrumentation work. If you need to disable this functionality, you can configure a manual setting in the local Dockerfile on the VM. There is a commented section near the top of the file that instructs you to uncomment a single line below which will disable the TIER Instrumentation functionality.
TIER: Release One
April 16, 2016
(Containerization Strategy)
Synopsis of
Trust and Identity in Education and Research
Package Delivery
The ultimate goal of TIER is the integration of community-developed open-source trust and identity software components into a manageable and complete identity and access management suite, supported by common campus practices.
NOTICE:
The distribution contains generally-available software components that have been tested by their respective engineering teams and the community. However, the container delivery mechanism (in the form of Virtual Machine Images) has not.
Therefore, this release should be considered a “first look” at the strategy as Docker containers and virtual-machine images themselves must be tested and refined through iterative adoption and feedback cycles from the campus practitioners.
Production deployment of these virtual machines is not recommended at this time.
Formative Work
In order to package and deliver the software in TIER Release One, considerable work had to be coordinated across myriad constituencies and disciplines. To meet the primary objective of Durable Standards and Practices identified by the community, campus practitioners and Internet2 staff produced the comprehensive set of work packages and convened the necessary conversations to ensure that needs of the primary recipients (campus adopters) would be met.
To properly align the efforts, resources such as assigned university staff, contractors and consultants had to be properly engaged. Levels of engagement range from one-third time to full-time equivalents. Additional partner relationships and resources will be retained as funding and a persistent scope of work evolves throughout the course of the program.
TIER relies heavily on several working groups to get the specification work done, involving more than 100 active, contributing participants from the community. These teams work to ensure complete and comprehensive software development, documentation, partner engagement, and campus engagement. Internet2 has also hired software developers, a project manager, and a vice president for trust and identity thanks to the funds provided by the 49 TIER investor institutions.
| Tip | ||
|---|---|---|
| ||
Obtaining the Virtual Machine Images
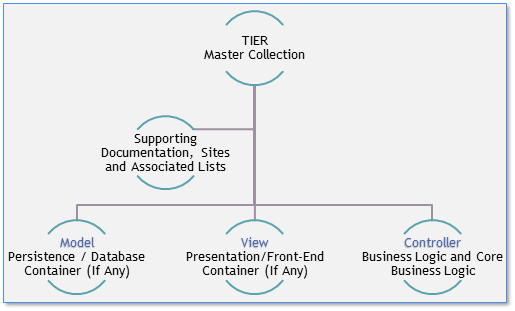
The TIER Component deliverables are roughly organized along the boundaries prescribed by the Model / View / Controller (MVC) Architectural pattern. The packaging team has had to make informed choices about where the operating system-level container boundaries must lie with respect to the layout in the virtual machine containers. Some components do not currently have a “View” element (such as Shibboleth) but will in the future. Exceptions are also made to the container choices where separation of the components cannot be reasonably accomplished at the “container” level. An example of this is the case with COmanage where View and Controller are combined in ONE container, while the Model is instantiated in another.
Despite the previous practical considerations, the structures generally follow this pattern:
Each container has its own start-up configuration requirements but the team’s goals have been to provide as consistent an experience as possible. Because of the zero-cost and highly versatile deployment choices available in Oracle’s Virtualization Software (VirtualBox), we chose to describe installation and configuration in those terms. For more information about VirtualBox, please refer to the information on Oracle’s website: https://www.virtualbox.org/wiki/Downloads
Packaging is delivered in the Open Virtualization Format (OVF) and the container is called an Open Virtual Appliance (sometimes also called Open Virtual Application, but we prefer the use of “Appliance”) (OVA).
The OVF format standard was formed by the Distributed Management Task Force, or DMTF, which is an industry working group comprised of over 160 member companies and organizations. The DMTF board is comprised of 15 technology companies and includes Dell, EMC, VMware, Oracle, and Microsoft. As announced at VMworld 2010, DMTF’s OVF standard was adopted as a National Standard by ANSI.
An OVF package structure consists of a number of files: a descriptor file, optional manifest and certificate files, optional disk images, and optional resource files (such as ISOs). The optional disk image files can be VMware vmdk’s, or any other supported disk image file. More information about the OVF format standard can be found at DMTF.Org’s web site (http://www.dmtf.org/standards/ovf).