...
Selecting a Strategy
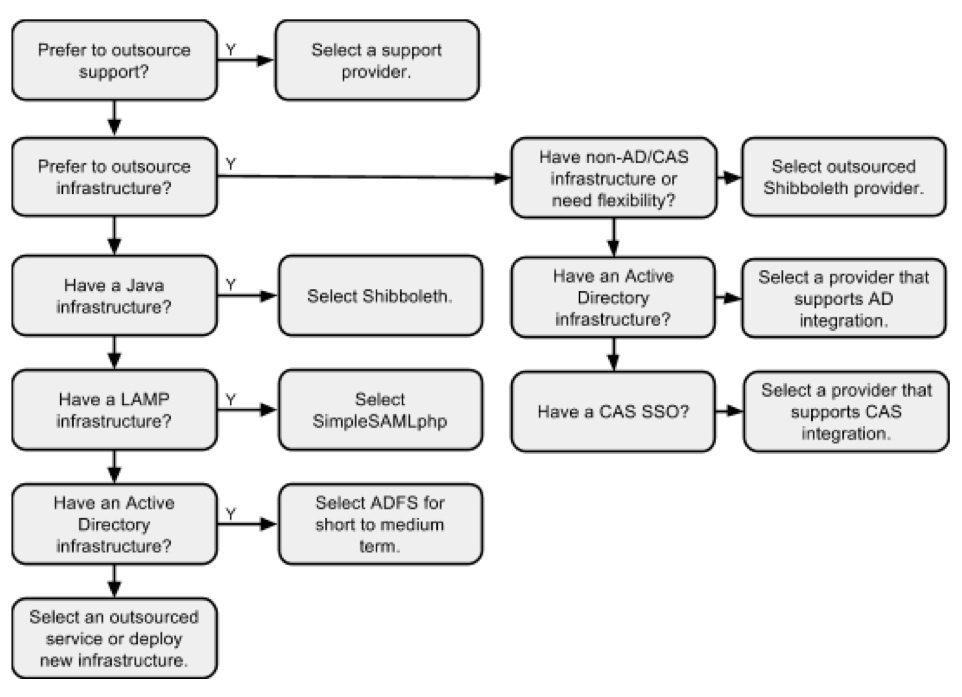
Choosing an IdP strategy for an institution will be based on many factors, most very unique to the institution. The following decision tree is intended help navigate the options:
Prerequisites for the IdP Strategy
Independent of how IdP service is deployed for a campus, there are a number of other issues that campus must address.
Manage the IdP Service Offering
Even when operation of the IdP is outsourced, it is still necessary to manage the service offering and the vendor providing that service.
Identity Provider Strategies for Common Campus Environments
Operate an IAMS
The campus must operate (or contract for operation of) an identity and access management system that tracks the lifecycle of community members’ affiliation with the campus. This includes maintenance of various information about those community members: name, addresses, affiliations, group memberships, record of identity proofing, entitlements, authentication credentials, etc.
Identity Management Policy
The campus must develop and maintain policy governing identity management functions. This is includes eligibility for campus affiliation, requirements for identity proofing, assurance requirements for services, etc.
Governance
The management structure and funding for identity management must be understood to assure alignment with campus management overall.
Recommendations for Future Work
The group considered several potential activities for future work by InCommon, TIER, and/or community members. These are listed here.
1.Activities for the InCommon administration or TIER.
1.1. Deploy or contract for a fullyfunctional, outsourced Shibboleth blessed by InCommon with InCommon participating in the management of the solution.
1.2. Establish a process for certifying IdP support vendors blessed by InCommon.
1.3. Create appliances for insourced operation including the CANARIE/SWAMID
IdP installer tool with configurations prebuilt for InCommon. These would likely
be distributed as virtual machine images.
1.4. Identify ways to facilitate InCommon members getting consultant help without a
lot of administrative overhead. This might be combined with a mentor program.
1.5. Conduct outreach to those institutions that are not engaged in federation and
would not know that alternatives for an IdP exist.
2. Community solutions with InCommon coordination.
2.1. Discuss ways to outsource an institution’s IdP to other InCommon members hosting the IdP
.2.
Identity Provider Strategies for Common Campus Environments Page 9
...
.
2.2. Develop a mentor program for InCommon Members to help campuses get started.
3. Second phase of the Alternative IdPs Working Group or another chartered group.
These solutions would have high value to the constituent group that the working group was tasked in addressing, i.e., institutions that do not have local resources, yet the work effort would not be as high as the recommendations above.
3.1. Develop criteria for assessing of IdP service vendors.
3.2. Identify and assess vendors. This would have to done repeatedly in order to
keep current and provide value.
3.3. Author a cookbook on deploying the IdP strategies, including technical
architecture, vendor selection, user support, operation, etc. Of these, we recommend the following actions be taken as next steps:
● Create appliances for insourced operation including the CANARIE/SWAMID IdP installer tool with configurations prebuilt for InCommon. Explore the method for easiest and most sustainable install possible which may be virtual machine, image, or simply the InCommon enhancements to the IdP Installer tool. (1.3)
● Conduct outreach to those institutions that are not engaged in federation and would not know that alternatives for an IdP exist. (1.5)
● Develop a mentor program for InCommon Members to help campuses get started. (2.2)
● Develop criteria for assessing of IdP service vendors. (3.1)
● Author a cookbook on deploying the IdP strategies, including technical architecture,
vendor selection, user support, operation, etc. (3.3)
Notes
● Items 1.1 (Deploy or contract for a fullyfunctional, outsourced Shibboleth blessed by InCommon with InCommon participating in the management of the solution) and 1.2 (Establish a process for certifying IdP support vendors blessed by InCommon.) are considered to be important tasks, but they rely on prior completion of 3.1 (Develop criteria for assessing of IdP service vendors).
● Item 1.5 (Reach out to those institutions that are not engaged in federation and would not know that alternatives for an IdP exist) is of particular importance as the target audience for these activities is institutions that do not currently participate in InCommon. Some of the ways in which outreach can be done include:
○ Publish case studies to make a basic case for federation and describing the benefits of being a participating member of the InCommon federation
○ Compile a list of organizations to target
○ Conduct interviews of CIOs from institutions who are not members of
InCommon
○ Create a “road show” for higher education venues, such as:
● Consortia like the Consortium of Liberal Arts Colleges (CLAC) Identity Provider Strategies for Common Campus Environments
Page 10
...