Jump to:
| Table of Contents | ||||||||
|---|---|---|---|---|---|---|---|---|
|
About Baseline Expectations 2
The second set of Baseline Expectations (BE2) adds three technical requirements aimed at improving security and the user experience. Implementation of BE2 is now under way. The InCommon Federation is expected to officially transition to BE2 on July 19, 2021.
The three BE2 elements are:
- Each Identity Provider and Service Provider must secure its connection endpoints with current and trusted encryption (TLS).
- All Identity Providers and Service Providers must comply with the SIRTFI international security response framework.
- All Identity Providers must include an error URL in metadata.
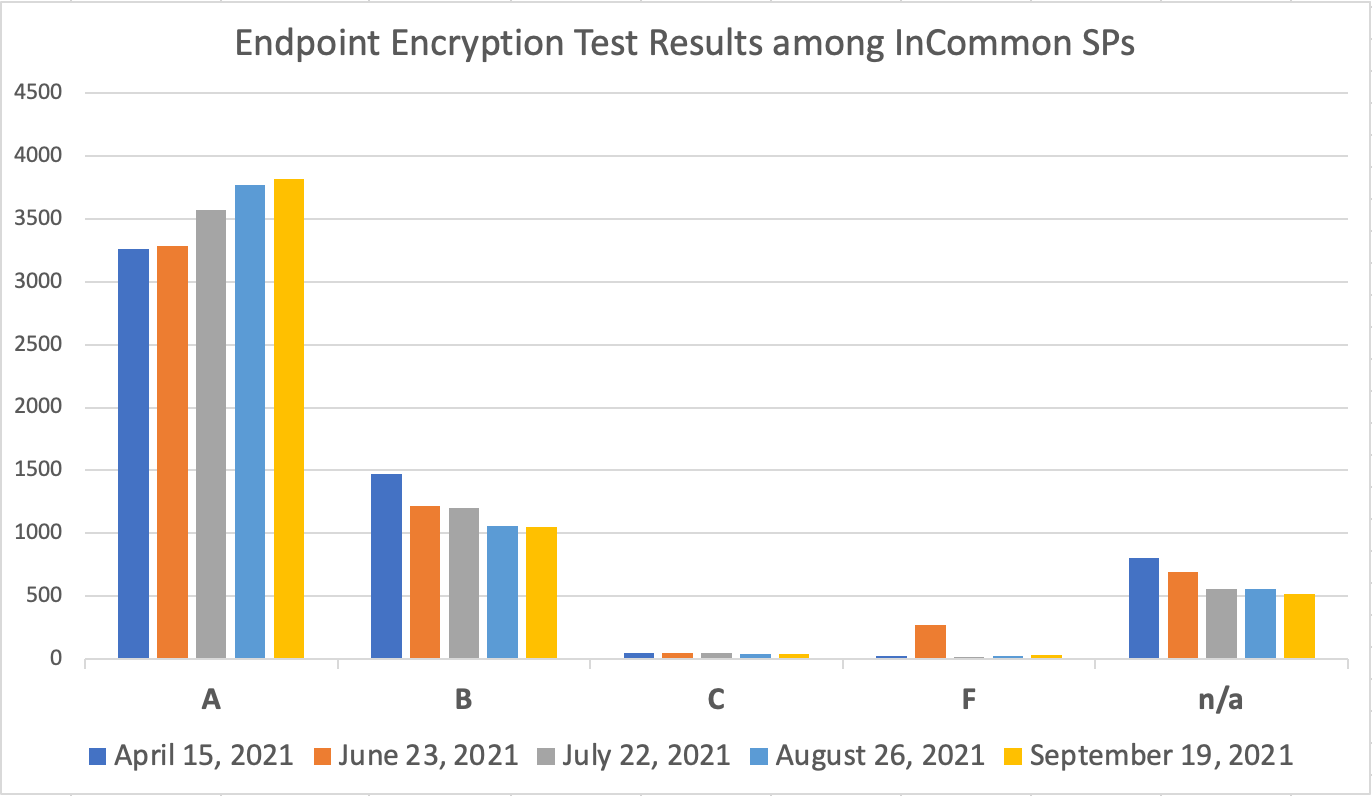
STATEMENT: All Identity Providers (IdP) and Service Providers (SP) service endpoints must be secured with current and community-trusted transport layer encryption.
When registering an entity (IdP or SP) in InCommon, all connection endpoints of that entity must be an https URL. The applied transport layer security protocol and associated cipher must be current and trusted by the community.
Popular security testing software such as the Qualys SSL Lab Server test offers a convenient way to test your server against these criteria and identify weaknesses. If using the Qualys SSL Lab Server test, an overall rating of A or better is considered meeting the requirements of the InCommon Baseline Expectations.
MORE: Clarification - Encrypt Entity Service Endpoints
STATEMENT: All entities (IdP and SP) meet the requirements of the SIRTFI v1.0 trust framework when handling security incidents involving federation participants
The SIRTFI trust framework v1.0 enables standardized and timely security incident response coordination among federation participants. When signaling and responding to security incidents within the federation, entity operators shall adhere to the process defined in the Sirtfi framework.
MORE: Clarification - Entity Complies with SIRTFI v1.0
STATEMENT: All IdP metadata must include an errorURL; if the condition is appropriate, SPs should use the IdP-supplied errorURL to direct the user to proper support.
IdP entity metadata must include a valid errorURL in its IDPSSODescriptor element.
An errorURL specifies a location to direct a user for problem resolution and additional support in the event a user encounters problems accessing a service. In SAML metadata for an IdP, errorURL is an XML attribute applied to the IDPSSODescriptor element.
When a service provider is unable to process an authentication assertion from an IdP, it may display within its error message a link to this URL to direct the user back to the IdP for additional assistance.