...
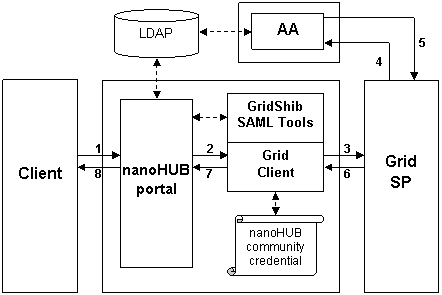
This deployment scenario is realized with current nanoHUB infrastructure, GridShib SAML Tools v0.1 and GridShib for Globus Toolkit v0.5.
| HTML |
|---|
| Wiki Markup |
{html} <OL> <LI> An unauthenticated browser user requests a Grid Resource via the nanoHUB portal.</LI> <LI> The nanoHUB portal authenticates the user (via LDAP), which initiates the following subsequence of events: <OL style="list-style-type: lower-alpha;"> <LI> The portal writes a dynamic config file (including one or more attributes) to disk.</LI> <LI> The portal passes the principal name and the authentication context (authentication method, authentication instant, and IP address) to the SAML Assertion Issuer Tool, which reads the config file created at the previous step.</LI> <LI>Using the nanoHUB community credential, the SAML Assertion Issuer Tool issues a SAML assertion and binds this assertion to a proxy certificate, which is written to disk.</LI> <LI> The portal invokes the Grid Client.</LI> </OL> </LI> <LI> Using the proxy certificate issued by the SAML Assertion Issuer Tool at step 2c above, the Grid Client authenticates to the Grid SP.</LI> <LI> The Grid SP parses the SAML assertion in the proxy certificate and issues an attribute query to the Attribute Authority (AA) at the nanoHUB IdP.</LI> <LI> The AA issues an attribute assertion and returns a response to the Grid SP.</LI> <LI> The Grid SP parses the attribute assertion in the response, makes an access control decision, and returns a response to the Grid Client.</LI> <LI> The Grid Client returns a response to the portal.</LI> <LI> The portal returns a response to the browser client.</LI> </OL> {html} |
...
Example
Here is an example of a SAML assertion bound to an X.509 proxy certificate in the case of attribute pull:
...
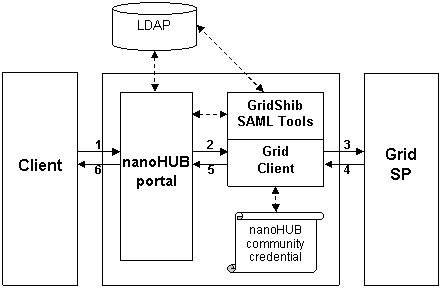
This deployment scenario requires GridShib SAML Tools v0.2 and GridShib for Globus Toolkit v0.6 (both of which are on the GridShib Online Roadmap). In this scenario, the functionality of the nanoHUB AA has been incorporated into the GridShib SAML Tools v0.2.
| HTML |
|---|
| Wiki Markup |
{html} <OL> <LI> An unauthenticated browser user requests a Grid Resource via the nanoHUB portal.</LI> <LI> The nanoHUB portal authenticates the user (via LDAP), which initiates the following subsequence of events: <OL style="list-style-type: lower-alpha;"> <LI> The portal passes the principal name and the authentication context (authentication method, authentication instant, and IP address) to the SAML Assertion Issuer Tool.</LI> <LI>The SAML Assertion Issuer Tool resolves attributes from the nanoHUB LDAP.</LI> <LI>Using the nanoHUB community credential, the SAML Assertion Issuer Tool issues a SAML assertion and binds this assertion to a proxy certificate, which is written to disk.</LI> <LI> The portal invokes the Grid Client.</LI> </OL> </LI> <LI> Using the proxy certificate issued by the SAML Assertion Issuer Tool at step 2c above, the Grid Client authenticates to the Grid SP.</LI> <LI> The Grid SP parses the SAML assertion in the proxy certificate, makes an access control decision, and returns a response to the Grid Client.</LI> <LI> The Grid Client returns a response to the portal.</LI> <LI> The portal returns a response to the browser client.</LI> </OL> {html} |
Note that the SAML Assertion Issuer Tool can resolve attributes from multiple attribute stores. In this case, attributes are resolved from nanoHUB LDAP.
...
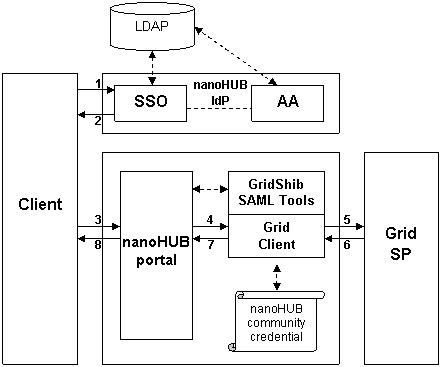
This deployment scenario assumes the nanoHUB portal is Shib-protected. The IdP depicted in the diagram is a fully configured nanoHUB IdP.
There is no IdP Discovery issue since the nanoHUB IdP is the only trusted IdP. Thus in the flow diagram above (and the discussion below), the flow begins with an authentication request at the nanoHUB IdP for simplicy of presentation.
| HTML |
|---|
| Wiki Markup |
{html} <OL> <LI> An unauthenticated browser user issues a SAML authentication request to the nanoHUB IdP.</LI> <LI> The SSO Service at the IdP authenticates the user (if necessary) and returns an authentication response (including attributes) to the browser.</LI> <LI> The browser user transmits the authentication response to the nanoHUB portal.</LI> <LI> The Shib-protected nanoHUB portal consumes the authentication response and initiates the following subsequence of events: <OL style="list-style-type: lower-alpha;"> <LI> The portal passes the Shib-issued SSO assertion (which includes the authentication context as well as nanoHUB attributes) to the SAML Assertion Issuer Tool.</LI> <LI>The SAML Assertion Issuer Tool binds the SSO assertion to a locally-issued SAML assertion (in the <CODE>Advice</CODE> element).</LI> <LI>Using the nanoHUB community credential, the SAML Assertion Issuer Tool binds this nested assertion to a proxy certificate, which is written to disk.</LI> <LI> The portal invokes the Grid Client.</LI> </OL> </LI> <LI> Using the proxy certificate issued by the SAML Assertion Issuer Tool at step 4c above, the Grid Client authenticates to the Grid SP.</LI> <LI> The Grid SP parses the SAML assertion in the proxy certificate, makes an access control decision, and returns a response to the Grid Client.</LI> <LI> The Grid Client returns a response to the portal.</LI> <LI> The portal returns a response to the browser client.</LI> </OL> {html} |
Example
Here is an example of a SAML assertion bound to an X.509 proxy certificate in the case of attribute push with local SSO:
...
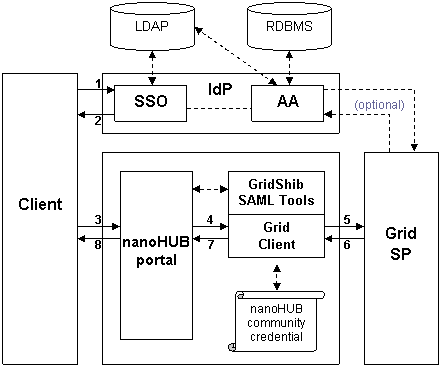
This deployment scenario supports cross-domain SSO. The IdP depicted in the diagram is any IdP trusted by nanoHUB.
In the flow diagram above (and the discussion below), we ignore the problem of IdP Discovery for simplicity of presentation. Thus the flow begins with an authentication request at the IdP.
| HTML |
|---|
| Wiki Markup |
{html} <OL> <LI> An unauthenticated browser user issues a SAML authentication request to a Shibboleth IdP.</LI> <LI> The SSO Service at the IdP authenticates the user (if necessary) and returns an authentication response to the browser. We assume the IdP supports attribute push and that the authentication response includes attributes.</LI> <LI> The browser user transmits the authentication response to the nanoHUB portal.</LI> <LI> The Shib-protected nanoHUB portal consumes the authentication response and initiates the following subsequence of events: <OL style="list-style-type: lower-alpha;"> <LI> The portal passes the Shib-issued SSO assertion (which includes the authentication context as well as campus attributes) to the SAML Assertion Issuer Tool.</LI> <LI>The SAML Assertion Issuer Tool binds the SSO assertion to a locally-issued SAML assertion (in the <CODE>Advice</CODE> element).</LI> <LI>Using the nanoHUB community credential, the SAML Assertion Issuer Tool binds this nested assertion to a proxy certificate, which is written to disk.</LI> <LI> The portal invokes the Grid Client.</LI> </OL> </LI> <LI> Using the proxy certificate issued by the SAML Assertion Issuer Tool at step 4c above, the Grid Client authenticates to the Grid SP.</LI> <LI> The Grid SP parses the SAML assertion in the proxy certificate, makes an access control decision, and returns a response to the Grid Client.</LI> <LI> The Grid Client returns a response to the portal.</LI> <LI> The portal returns a response to the browser client.</LI> </OL> {html} |
Note that between steps 5 and 6 the Grid SP may decide to query the AA at the IdP. There is sufficient information in the nested assertion (namely, the IdP entityID and SAML Subject) to perform such a query.
...