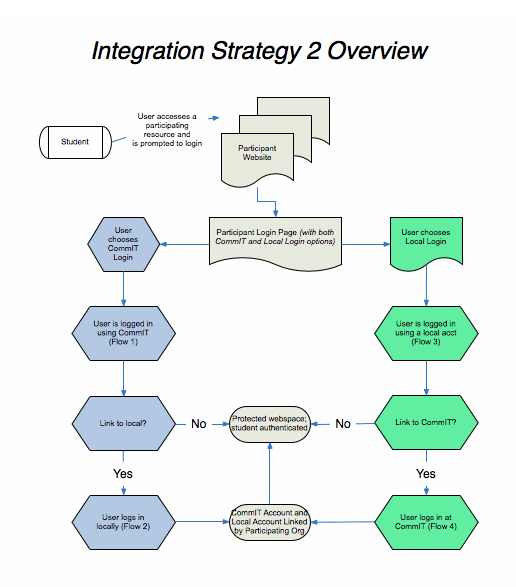
...
Each scenario has a matching story that demonstrates how the flow might be used. There are separate flow diagrams to depict modes of the integrated system, but they compose into a single, unified decision tree. The flow as depicted begins when the user attempts to access a protected service at a participating organization, although it could be invoked at various points on various sites. The flow ends when the user is able to access the desired secured content, or with display of appropriate error and help information when the user is unable to access the resource.
Other flows, such as the aggregation of attributes about a principal from all participants in the CommIT ecosystem at the end stage of the application process, are out of scope for this document, which addresses only authentication.
...